Introduction
Businesses of all types and sizes are facing an unprecedented threat to the data they utilize and store in the natural course of their operations. Hackers and others who are not authorized to access this information are using sophisticated techniques to work their way into organizations by a variety of methods including social engineering. This type of hacking technique has been identified as the most widely used method (Ashford, 2016) and is considered one of the leading threats to information security today (Mitnick & Simon, 2002; Airehrour, Nair, & Madanian, 2018). Social engineering has specifically been identified as one of the top three security-related issues in industries such as manufacturing, educational services, and food services (DBIR, Verizon, 2021).
Social engineering can be defined as the act of manipulating human beings, most often with the use of psychological persuasion, to obtain unauthorized access to systems containing data, documents, and general information that the social engineer should not have access to (Mitnick & Simon, 2002; Tetri & Vuorinen, 2013; Heartfield & Loukas, 2015). Social engineering today mostly focuses on the information security realm and the potential threats that face both large and small businesses as well as individuals.
The purpose of this research study is to explore whether demographic characteristics of employees and owners of small businesses can predict social engineering susceptibility. The study utilized the Human Aspects of Information Security Questionnaire (HAIS-Q) created by Parsons, McCormac, Butavicius, et al. (2014). When completed, the questionnaire provides an information security awareness score based on the responses provided by the participant. This score was then converted to a social engineering susceptibility score based on the assumption in the literature that the higher an individual’s information security awareness, the lower the individual’s susceptibility to social engineering (Butavicius et al., 2007; Janczewski & Fu, 2010).
Literature Review
A literature review was conducted of any relevant and pertinent research studies. Social engineering is a complex and multifaceted event that lacks both a conceptual framework (Janczewski & Fu, 2010) and a practical, real-world framework (Williams, Hinds, & Joinson, 2018) through which to study its occurrence. Several researchers have had to rely on theories and models from other disciplines to better understand the nuances contained within a social engineering attack.
Demographics as a Determinant of Social Engineering Susceptibility
Susceptibility to social engineering is an important component of the concept. Individuals’ cognitive ability (Montanez, Golob, & Xu, 2020) and how they process information influence their susceptibility to phishing attacks (Vishwanath, et al. 2011). Several researchers chose to study an even more rudimentary level of measuring susceptibility in individuals by analyzing their basic demographic data.
Gender
Gender has been studied by multiple researchers. Several studies determined women were more susceptible to social engineering attacks than men (Sheng et al., 2010; Jagatic et al., 2007), and this includes opening phishing emails (Goel, Williams, & Dincelli, 2017), responding to spear-phishing emails (Halevi, Memon, & Nov, 2015), and using social networking websites (Algarni, Xu, & Chan, 2015). It has been suggested that men understand technology more than women, so they were less likely to fall victim to a social engineering attempt in which confidential information was requested (Sheng et al., 2010). Another explanation theorizes that individuals’ emotional responses could potentially outweigh rational thinking if a characteristic of that individual is triggered by some component of the attack (Halevi et al., 2015). Depending on emotional states, employees might respond to a persuasion technique when experiencing one emotion compared to when experiencing another (Van Kleef, van den Berg, & Heerdink, et al., 2015).
Emotions can be a powerful influencer in changing a person’s thoughts and attitudes. In fact, the use of emotions is already widely used in politics and advertising so it makes sense that it would also be used in an organizational setting (Van Kleef et al., 2015). While it has been identified that emotions are common in organizations, a further distinction can be made as to whether emotions are used by males or females. Indeed, people’s perceptions of which gender displays emotion impacts the interpretation of that emotion (Salerno & Peter-Hagene, 2015). Researchers found that opinions expressed by emotional women do not influence as many people as the opinions expressed by emotional men (Salerno & Peter-Hagene, 2015). This fact relates to social engineering attackers and victims as there can now be a gender component used to determine how one can be more persuasive.
The same study also concluded that when men express anger, they are viewed as more powerful and persuasive and, in fact, even more credible than if the emotion was not present. Perhaps a male social engineer, showing anger in an appropriate situation, can convince an unsuspecting employee to provide confidential information. However, anger expressed on behalf of women was not as influential as when males used it. In the study, Salerno and Peter-Hagene (2015) found that people who viewed a woman expressing anger believed the woman to be more emotional and not persuasive in changing the views of others. These studies (Van Kleef et al., 2015; Salerno & Peter-Hagene, 2015) focused their attention on the characteristics of the source rather than the recipient but in terms of social engineering understanding, the demographic and psychological traits of both participants in the attack can help further the understanding of susceptibility to social engineering.
Continuing with studies on gender and social engineering, other researchers determined that more men than women were likely to become victims of social engineering (Happ, Melzer, & Steffgen, 2016) and others determined that gender was not significant in terms of predicting vulnerability to phishing scams (Moody, Galletta, & Dunn, 2017). Based on these contradictory findings, further research is suggested by the authors to validate the significance of gender on social engineering susceptibility.
Age
Age is another demographic explored by researchers that could potentially relate to social engineering susceptibility. One study determined that those in the age range of 28 – 38 were less likely to provide their own personal information when requested (Airehrour et al., 2018) while other studies determined that younger people were more likely to reveal a password when asked (Happ et al., 2016), were more susceptible to phishing attacks (Sheng et al., 2010), and were more susceptible to social engineering through the use of social networking websites (Algarni et al., 2015). Jagatic et al. (2007) studied the use of phishing emails that contained information found on recipients’ social networking sites. The phishing emails were sent to university students, and it was determined that freshmen were slightly more susceptible to opening the emails than seniors. Related to the discussion on gender, the study also determined that a phishing email sent by the opposite gender of the recipient had a greater chance of success than one sent by the same gender (Jagatic et al., 2007). Contributing to contradictory findings, Moody et al. (2017) determined that age was not a significant predictor of vulnerability in terms of phishing attacks. However, their research only included participants of a similar age in a single class at a university.
Training
Training has been explored as it relates to social engineering susceptibility. Sheng et al. (2010) determined that the use of educational materials decreased the likelihood that individuals would provide information in response to a phishing email. Similarly, Airehrour et al. (2018) suggested that awareness training is a critical component of mitigating attacks, and Heartfield & Loukas (2015) proposed that training helps individuals identify cues in social engineering attempts. Sumner, Yuan, Anwar & McBride (2022) determined that detection of phishing emails increased by 8% after anti-phishing training. Some studies question the impact of social engineering training by claiming it is “too static and unresponsive to the changing cyber domain” (Williams et al., 2018, p.9) or that it is limited in its ability to affect people because knowledge imparted in the trainings is usually overshadowed by the impact of urgency cues in particular social engineering situations (Vishwanath et al., 2011).
Cultural Identity
Cultural differences have been studied in the context of social engineering susceptibility. Bullee et al. (2015) studied Cialdini’s authority principle of persuasion (2007) and proposed that cultural differences in adherence to authority impact the strength with which it is used as an influencer. Butavicius et al. (2017) determined that the cultural focus on individual rather than group needs was a strong predictor in determining whether people can distinguish between safe and unsafe emails. Williams et al. (2018) studied phishing susceptibility and highlighted the importance of understanding differences between communication and email styles because of cultural variations.
Other Variables
Other lesser-studied variables researched to predict social engineering susceptibility include length of employment and rank. Research has shown that newer employees could potentially be more susceptible to social engineering since they most likely do not know all the employees or contacts they would be communicating with on the job and as a result, would be less likely to identify phishing emails (Williams et al., 2018). This finding is somewhat contradictory to another study that determined that when the sender of an email is known, the susceptibility to social engineering of the recipient increases (Moody et al., 2017). Newer employees would most likely not know the senders of emails they receive which would mean they are less susceptible in terms of falling victim to a phishing email.
Although studied infrequently, the rank of an employee can be used to help predict susceptibility to social engineering. Uebelacker & Quiel (2014) suggested that a manager, or someone with a higher rank, has greater access and ability to share important confidential information. However, they concluded that every individual has the potential to provide varying degrees and amounts of information to social engineers so rank is not important.
To the best of the researcher’s knowledge, there have been no studies that explored other variables as predictors of social engineering susceptibility including education or hours worked, as well as studies that have been conducted in a small business setting. Most of the studies have been done in university settings with college students, staff, or faculty (Jansson & von Solms, 2013; Vishwanath et al., 2011; Wright et al., 2010; Van Kleef et al., 2015; Snyman & Kruger, 2016; Zheng et al., 2018; Vishwanath, Harrison, & Ng., 2016; Moody et al., 2017).
Small Business
Small businesses have the potential to be one of the most susceptible types of businesses to social engineering (Social-Engineer, 2018; Aguilar, 2015), and these attacks are increasing in occurrence (Harris, 2018). They often lack resources, both technical and human, to protect themselves from outside threats (Hiscox, 2018). These businesses usually understand the risks they face and take appropriate actions that align with their limited budgets. However, very rarely are they able to implement full-scale security safeguards to improve their resilience and reduce susceptibility (FSB, 2016), especially to business email compromise (BEC) schemes which are considered to be the most frequent type of attack for small businesses (Harris, 2018).
After a data breach or social engineering attack, a small business usually needs at minimum two days to return to normal business operations and often it takes an entire week (FSB, 2016). This downtime for small businesses can have a substantial impact on their profits and viability to continue operations in the future (Hiscox, 2018). About half of small businesses that are victims of cyberattacks are forced to go out of business in the six months following the attack (LeClair, 2015).
Many small businesses also underestimate the amount of risk they face in terms of data breaches and social engineering attacks and become easily overwhelmed with trying to understand the significant risks they face on a daily basis (Social-Engineer, 2018). The limited number of staff is usually performing multiple roles in the company, and cybersecurity protections tend to rank lower on the list of priorities when compared to the other critical functions that must be completed in the course of business (FSB, 2016). It is for this reason that small businesses are appealing targets to attackers. These companies can be used as a gateway to obtain access to larger companies that likely have better security protections in place (Aguilar, 2015).
Human Aspects of Information Security Questionnaire (HAIS-Q)
The human aspects of information security questionnaire (HAIS-Q) was created by Parsons, McCormac, Butavicius, et al. (2014) to study the relationship between knowledge, attitude, and behavior and information security policies. The questionnaire was originally developed as a result of a quantitative and qualitative study with over 200 employees from government organizations in Australia (Parsons, McCormac, Pattinson, et al., 2013). They attempted to measure information security awareness among employees and managers in these organizations. While employees scored at acceptable levels for knowledge, attitude, and behavior, the scores were higher specifically for the knowledge component. The researchers concluded that employees may have high knowledge regarding information security policies, but their behavior does not necessarily align with their level of knowledge. This conclusion was further supported by the qualitative interviews performed with members of management (Parsons, McCormac, Pattinson, et al., 2013).
This initial study served as the foundation for the development of the HAIS-Q in which the researchers created seven focus areas to measure knowledge, attitude, and behavior of employees when using a work computer. The questionnaire has been tested for validity and reliability (Parsons, McCormac, Butavicius, et al., 2014; Parsons, Calic, et al., 2017). As of 2017, over 1,500 employees from a variety of industries in Australia have completed the HAIS-Q. Training and education programs in organizations can be tailored to specific employee needs based on the result of the HAIS-Q (Parsons, et al., 2017).
The HAIS-Q has been widely used in research studies. Butavicius, et al. (2017) used the questionnaire in conjunction with Cialdini’s (2007) principles of persuasion on business students from an Australian university. The researchers created online scenarios containing three types of emails including phishing, spear-phishing, and authentic, along with three of Cialdini’s (2007) principles, authority, social proof, and scarcity, as means of social engineering techniques. Participants in the study were asked to judge the safety of the various emails they were shown. At the end of the lab-based simulation, participants completed the HAIS-Q. Butavicius, et al. (2017) determined that culture and information security awareness were two of the strongest predictors of whether the participants were able to distinguish between safe and unsafe emails. Higher information security awareness was correlated with identification of malicious emails.
Pattinson et al. (2017) used the HAIS-Q in a study on bank employees in Australia and in another study with 500 employees from a variety of industries. The researchers concluded that information security awareness of the bank employees was about 20% higher than those in other industries. They studied the use of training in these organizations, and in a somewhat contrary finding to what they expected, the researchers determined that only 16% of the bank employees had experienced a formal education in information security compared to 27% of the generalized employee group from multiple industries.
The main focus of the HAIS-Q is to measure information security awareness, and several studies have found a link between awareness and susceptibility. Professionals in the information technology industry attribute social engineering success to the absence of information security awareness. Interviews with these industry professionals revealed to the researchers that people are simply unaware of issues in information security today, social engineering being one of them (Janczewski & Fu, 2010). Butavicius et al. (2017) concluded that information security awareness, as a self-report measure in the HAIS-Q, led to better detection and identification of suspicious emails.
To further support these findings, researchers have used interventions to bring awareness of information security issues to individuals and then determine if there is a connection between these interventions and susceptibility to social engineering (Bullee et al., 2015; Montanez, Golob, & Xu, 2020). Williams et al. (2018) used focus groups to measure the effectiveness of email banners as a means of brief communication with the participants. These banners urged viewers of emails to consider the safety and validity of the messages before clicking on any links. The banners brought an increased sense of awareness to people, making them more likely to distinguish between safe and unsafe emails, and therefore making them less susceptible to social engineering attacks via phishing emails.
Bullee et al. (2015) used three types of interventions, a leaflet, key chain, and poster, that contained reminders to employees about information security issues related to social engineering, sharing access, and password / PIN security, respectively. These interventions served as a method of awareness and significantly reduced the likelihood that employees would share their work keys when requested. Those employees who did not receive the intervention were almost three times more likely to comply with the request than those who experienced one of the three interventions (Bullee et al., 2015).
The HAIS-Q measures three components of an individual’s security awareness: knowledge, attitude, and behavior. A somewhat similar model based on the comparable foundational principles of the HAIS-Q is found in the suspicion, cognition, and automaticity model of phishing susceptibility (SCAM) as postulated by Vishwanath et al. (2016). This model was tested in two studies that involved phishing emails and suggested that cognitive ability of individuals can be piqued by suspicions about various types of cues. In addition, there are varying levels of automaticity, or routineness, in people’s actions, especially as it relates to email behavior. The components of the model mentioned here can serve to detract from attempts to train individuals on social engineering susceptibility and therefore influence their knowledge, attitude, and behavior (Vishwanath et al., 2016).
Williams et al. (2018) acknowledged the importance of these previously mentioned cognitive capabilities in their study but suggested the application of standard, accepted practices and procedures to better understand susceptibility. One specific practice is that of organizational cognitive pressure which could lead to an increase in susceptibility to phishing emails. The larger point found in this research is that additional factors need to be considered when determining susceptibility. The researchers acknowledged their inability to collect demographic information from participants in their study (Williams et al., 2018) which could have added another layer to the data they collected from two different organizations regarding phishing susceptibility.
Methodology
The purpose of this research study was to determine if demographic features of employees in small business impact susceptibility to social engineering as measured on the Human Aspects of Information Security Questionnaire (HAIS-Q). A cross-sectional survey was used and data was collected at a single point in time, since internal and external factors could impact survey results. Internal factors can include the availability or pervasiveness of employee training and external factors can include widely publicized data breaches or trending economic/social issues, all of which could impact employee responses to survey questions. The survey collected data using the REDcap online platform which allowed employees to complete the survey on a computer or mobile device.
Sample
The population in this study included a convenience sample of employees and owners from small businesses. They must be at least 18 years of age, employed by a small business in Northeastern Pennsylvania with less than 25 employees, and must have a company-issued email address along with access to a computer or mobile device. Very few research studies have been conducted on social engineering in small businesses making this population an ideal one to study.
When potential participants attempted to begin the survey, they were asked whether they worked for a small business in Northeastern Pennsylvania that employs less than 25 people and whether they have a company-provided email address. If potential participants answered no to either of these questions, the survey would not continue ensuring only those that continued to the HAIS-Q and demographic questions fit the criteria outlined by the researcher.
Instrumentation
HAIS-Q.
The Human Aspects of Information Security Questionnaire (HAIS-Q) was originally designed by Parsons, McCormac, Butavicius, et al., (2014) to measure information security awareness based on the components of knowledge, attitude, and behavior of individuals. They specifically identified focus areas to measure the various components including password management, email use, internet use, social networking site use, incident reporting, mobile computing, and information handling. A modified version of the HAIS-Q was used in this research study. All focus areas identified previously were used in the study except for social media use and incident reporting. Employees were prompted to read a statement related to their knowledge, attitude, or behavior about the focus areas of password management, email use, internet use, mobile devices, and information handling.
Participants provided answers using a 5-point Likert scale with possible answer choices including Strongly Agree, Agree, Neither Agree nor Disagree, Disagree, and Strongly Disagree. The list of questions is provided in the appendix in Figure 2.
Each statement in the HAIS-Q has point values assigned to the answers based on the Likert scale. For positively framed statements, Strongly Agree was worth 5 points, Agree was worth 4 points, Neutral was worth 3 points, Disagree was worth 2 points, and Strongly Disagree was worth 1 point. Negatively framed statements were scored as follows: Strongly Agree was worth 1 point, Agree was worth 2 points, Neutral was worth 3 points, Disagree was worth 4 points, and Strongly Disagree was worth 5 points. Each participant’s survey resulted in an overall score which totaled the points assigned from each statement answer. The modified HAIS-Q used in this survey contained 45 statements meaning that the highest possible total score was 225 and the lowest possible score was 45 assuming all questions were answered. This survey was intended to measure information security awareness so the higher the score, the higher the employee’s awareness. If an employee has high information security awareness, then the employee will be ranked low on susceptibility to social engineering. Conversely, if an employee has low information security awareness, then the employee will be ranked high on susceptibility to social engineering.

Figure 1. Modified HAIS-Q scoring. This figure provides the range of possible scores on the modified version of the HAIS-Q, ranking respondents from low to high susceptibility to social engineering.
Demographic Data Collection
The second data collection instrument used in this survey asked respondents to answer questions related to their demographics and current work situation including gender, age, education, length of employment with a company, hours worked, industry, information security awareness training, rank, and cultural identity. Demographic questions can be found in Figure 3.
Procedures
An invitation to participate in this survey was emailed to the potential participants’ company email addresses directly from the researcher and posted on social media pages including Facebook and LinkedIn. The survey was open to participants for a total of eight weeks.
Results
The data set consists of 95 participant responses collected over an eight-week period. The Kolmogorov-Smirnov test of normality shows that the data is normally distributed (ISA Score, p = .20; Knowledge Score, p = .20; Attitude Score, p = .09; Behavior Score, p = .20). Slightly more than half of the participants were male (n = 54), and the mean age of participants was 42.6 years old (sd +/- 12.5). Most participants had a maximum education of a bachelor’s degree, worked at their respective companies for less than ten years, identified as owners of the company, received awareness training at least once per year over the last three years, and identified as American.
The totals of the respondents’ knowledge, attitude, and behavior scores in the HAIS-Q were combined to determine an information security awareness (ISA) score. The mean ISA score is 185.9 (sd +/- 21.92), while the median is 186 (118 – 225).
The ISA score was then converted to an employee susceptibility score with the understanding that the higher the ISA, the lower the susceptibility (Janczewski & Fu, 2010; Parsons, McCormac, Butavicius, et al., 2014; Pyzik, 2015). The ISA scale includes a possible score range from 45 – 225. This scale was converted to an inverse susceptibility scale ranging from 0 – 100. The following formula was used for the conversion: ((ISA Score – 225) * (100/180) * – 1). The mean susceptibility score is 21.71 (sd +/- 12.18), while the median is 21.67 (0 – 59.44).
Multiple Regression
Scale level variables including the independent variables, age and weekly hours worked, and the dependent variable, susceptibility score, were examined for outliers. Any outliers were checked by analyzing z-scores, and none of the outliers showed z-scores +/- 3.29. Multivariate outliers were examined using Mahalanobis distance. The minimum (4.45) and the maximum (25.58) were below the critical cutoff of 29.59. Cook’s distance was found to be 0.207, well below a value of 1. None of the coefficient correlations exceeded a value of 0.3 and the variance inflation factor was below 10, both of which do not suggest any issues with multicollinearity.
A multiple linear regression was calculated to predict participants’ susceptibility score based on their gender, age, education, length of employment, average number of hours worked per week, industry, training, rank, and cultural identity. The regression equation was not significant (F(10, 80) = .583, p > .05) with an R2 of .068. None of the independent variables are significant predictors of susceptibility score. See Table 1.
Pearson Correlations – Knowledge, Attitude, and Behavior
A Pearson correlation coefficient was calculated for the relationship between participants’ knowledge, attitude, and behavior scores. A strong positive correlation was found between knowledge and attitude (r (93) = .698, p < .001), between knowledge and behavior (r (93) = .755, p < .001), and between attitude and behavior (r (93) = .713, p < .001) indicating a significant linear relationship between the two variables in each grouping respectively. As each participant’s category score increased, the scores in the other two categories increased.
A strong negative correlation was found between knowledge and susceptibility (r (93) = -.921, p < 0.001), between attitude and susceptibility (r (93) = -.878, p < 0.001), and between behavior and susceptibility (r (93) = -.907, p < 0.001). As knowledge, attitude, and behavior scores increase, susceptibility to social engineering decreases.
Knowledge, Attitude, and Behavior Scores as Predictors
A simple linear regression was calculated to determine if the knowledge score predicts the attitude score. The regression equation was significant (F(1, 93) = 88.22, p < .001) with an R2 of .49. Participants’ predicted attitude score is equal to 33.28 + .541 (knowledge score). Participants average attitude score increased by .54 for each point increase in knowledge. See Table 2.
A simple linear regression was calculated to determine if the attitude score predicts the behavior score. The regression equation was significant (F(1, 93) = 96.28, p < .05) with an R2 of .51. Participants’ predicted behavior score is equal to 13.53 + .75 (attitude score). Participants average behavior score increased by .75 for each point increase in attitude. See Table 3.
A multiple linear regression was calculated to determine if knowledge and attitude scores predict the behavior score. The regression equation was significant (F(2, 92) = 81.07, p <.05) with an R2 of .64. Participants’ predicted behavior score is equal to 13.48 + .41 (knowledge score) + .38 (attitude score). Participants’ behavior scores increased by .41 for each increase in knowledge score and by .38 for each increase in attitude score. See Table 4.
Training
The mean susceptibility score of participants who received different amounts of cybersecurity awareness training were compared using a one-way ANOVA. A significant difference was found among those with varying levels of cybersecurity awareness training (F(4,90) = 2.78, p < .05). However, both Tukey’s HSD and Duncan’s post hoc tests showed no differences among the groups. As a result, the LSD post hoc procedure was run with an adjustment to the alpha level needed to achieve statistical significance downward by dividing the original alpha (.05) by the ten comparisons that were made. This created a new alpha level of .005. No significant differences could be found after making that adjustment. However, a negative directional trend can be observed in which more training results in a lower susceptibility score. See Table 5.
Training (Recode)
Because a significant difference was found in the previous analysis on training and a negative directional trend was observed in relation to training and susceptibility score, the training variable was recoded into three groups: no training, training received one to three times on average for the year, and training received more than three times on average during the year. This recode allowed for a better exploration of the participant groups based on what can be perceived as no training, some training, or a lot of training, respectively.
The mean susceptibility score of participants who received different amounts of cybersecurity awareness training were compared using a one-way ANOVA. A significant difference was found among those who received different amounts of training (F(2, 92) = 3.51, p < .05). Tukey’s HSD was used to determine the nature of the difference between the varying amounts of training. This analysis revealed that participants who received cybersecurity training more than three times on average per year had a significantly (p < .05) lower susceptibility score (M = 13.97, sd = 13.16) than participants who received no training (M = 24.02, sd = 11.01). Participants who received training between one and three times on average per year (M = 21.95, sd = 12.21) were not significantly different from either of the other two groups. See Table 6.
Discussion
This research study did not find that any of the demographic characteristics measured in the survey were able to predict susceptibility to social engineering. While the other studies noted in the literature were not conducted on small business owners and employees, the findings from this study were in contradiction to some previous findings which found that women more than men were susceptible to social engineering attempts (Sheng et al., 2010; Jagatic et al., 2007, Halevi et al., 2015, Algarni et al., 2015) and to another study which found that men more than women were susceptible to social engineering attempts (Happ et al., 2016). This study was not able to clarify or confirm their findings, and one reason could be because of the population studied. This study was unique in that it was conducted in small businesses in Northeastern Pennsylvania rather than on college students, faculty, or staff (Moody et al., 2017; Jagatic et al. 2007; Jansson & von Solms, 2013; Vishwanath et al., 2011), other industries such as government (Parsons, McCormac, Pattinson, et al., 2013), or large companies in healthcare, retail, education, construction, and manufacturing (Parsons, McCormac, Butavicius, et al., 2014).
Moody et al. (2017) determined that age was not significant in predicting susceptibility to phishing attacks, and the results of this study support those findings. It should be noted that the age range of participants in this study (19 – 75) was different from the smaller range of college-age students included in that study. The research described here, however, is in contradiction to the study by Sheng et al. (2010) which determined that those in the age range of 18 – 25 were more likely to fall victim to a phishing scam.
While cybersecurity awareness training was found to not be a significant predictor of social engineering susceptibility, a positive directional trend can be found in knowledge and behavior scores when more training is received by employees. Consequently, a negative directional trend can be found in susceptibility scores when more training is received by employees. Because of these trends, the researcher explored the training variable by grouping responses in a different way. In the demographic section of the questionnaire, participants were asked to think about the last three years and report how many times, on average per year, they received cybersecurity awareness training. After grouping responses together to run an analysis on those who received no training, those who received training on average one to three times per year, and those who received training on average more than three times per year, a significant difference was found in the knowledge score and overall susceptibility score between those who received no training and those who received training more than three times per year. These results support previous findings by Airehrour et al. (2018) and Heartfield & Loukas (2015) that awareness training has a substantial impact in mitigating social engineering attempts. This is an important concept for small business owners to consider as part of their information security plan, if one exists. Awareness training can have a significant impact on employees of small businesses and help them if a social engineering attack is attempted. In addition, the findings also support research by Grassegger & Nedbal (2021) who determined that individuals who exhibit non-risky behavior tend to have a high information security awareness.
The supplemental analysis in this research study shows that significance was found in terms of the three categories found in the HAIS-Q: knowledge, attitude, and behavior. Knowledge has been shown to be a significant predictor of attitude and attitude has been shown to be a significant predictor of behavior. Both knowledge and attitude have been shown to be significant predictors of behavior. These results support the findings and the hypothesis proposed by Parsons, McCormac, Butavicius, et al. (2014) in which knowledge of information security policies leads to a better attitude towards these policies. In addition, increased knowledge and attitude support less risky behavior as measured by a self-report mechanism. Their findings and those described here provide support for their HAIS Model, specifically the knowledge, attitude, and behavior (KAB) component.
The results are important in the context of the population studied here because small businesses should be encouraged to increase employees’ knowledge of cybersecurity and social engineering issues to impact attitude, and most importantly, to influence their behaviors in the workplace. Small business owners and managers should attempt to determine how they can make their employees more knowledgeable if they want to see them display appropriate behaviors when faced with a social engineering attempt.
The training variable is a unique demographic characteristic since it is one that can be easily changed unlike gender, age, or cultural identity. To alter a participant’s response to the training question, one simply has to provide training to the employee. The significance of this variable was not apparent in the multiple regression analysis but later became apparent when ANOVAs were analyzed on the three different options: no training, some training, and a lot of training.
Two of the variables studied in this research, cultural identity and industry, did not receive enough responses in any of the response categories to thoroughly make a determination as to the significance of these variables on social engineering susceptibility. The survey could be expanded to better capture the cultural identity of participants in a more culturally diverse population rather than Northeastern Pennsylvania to determine if there is support for prior research findings on the importance of culture (Bullee et al., 2015; Butavicius et al., 2017; Williams et al., 2018).
This study helped to fill a gap in the published social engineering research since it studied the small business population. As previously stated, small businesses comprise the majority of businesses in the United States (SBA.gov, 2018), and a successful social engineering attack on these businesses can be detrimental to the ability of the organizations to withstand an attack of this type (LeClair, 2015).
Even though none of the demographic variables studied here have been found to be significant predictors of social engineering susceptibility, these findings have major implications for the future of small businesses and how they choose to proceed in protecting themselves, if at all, from social engineering attacks.
Implications
The results of this study suggest that demographic characteristics of employees in small businesses are not significant predictors of social engineering susceptibility. This can provide some reassurance to small business owners that they and their employees are not more or less susceptible to social engineering attacks based on their demographic characteristics measured here, most of which are out of the control or at least limited control of the owner or employee. These results suggest that there is something else that contributes to social engineering susceptibility, possibly something better able to be controlled by the owner or employee. Small businesses should not view some employees as more of a risk than others simply based on their demographic characteristics. Other contributing factors to susceptibility, rather than demographics, could include psychological characteristics such as fear of losing / eagerness to gain (Goel et al., 2017; Cheung-Blunden et al., 2018), likability and trust (Flores et al., 2013; Guadagno et al., 2013), and boredom proneness (Moody et al., 2017).
Participants had possible information security awareness scores in the range of 45 – 225 with a lower score suggesting higher susceptibility to social engineering. Small business owners and employees in Northeastern Pennsylvania scored relatively high on the information security awareness scores with less than 10% of the respondents (n = 9) scoring less than 161 points. Even though prior research suggests that 2/3 of small businesses are concerned about cybersecurity issues (Hiscox, 2018), information security awareness is relatively high in the small business population surveyed here. While this does not necessarily alleviate concerns they might have, it does offer some encouragement that small businesses might be more aware of cybersecurity issues than previously thought and can actively work toward ways to reduce the success of attacks on their business. This can include involving employees in creating an information security plan since most of them have a moderate level of information security awareness. The small number of employees in these businesses makes this a manageable solution to implement.
Because knowledge has been determined to be a significant predictor of attitude and attitude has been determined to be a significant predictor of behavior, small businesses should focus on ways to increase employee knowledge in an attempt to influence their behavior in terms of cybersecurity issues. Related to these findings, even though cybersecurity awareness training has not been found to be a significant predictor of social engineering susceptibility, those employees who received training more than three times per year on average have lower susceptibility scores than those employees who received no training.
Although small businesses usually operate on limited budgets and might not allocate funding towards training (Jackson, 2018), the results indicate that training employees on cybersecurity awareness could have an impact on their likelihood of falling victim to an attempted social engineering attack. Small business owners should consider various training options for their employees especially on a continuing basis several times per year since this can strengthen the information security protections of the company.
An important distinction should be made regarding the difference between information security awareness and information security awareness training. Awareness can simply consist of sending reminder emails to employees or posting memos in various office locations to encourage individuals to be mindful of potential social engineering attacks. Awareness training, however, is more involved because it includes these educational efforts while also being interactive. This type of training focuses more on modifying individual behaviors in the workplace rather than simply trying to enforce rules and regulations (Newcombe, 2016).
This issue of security awareness training is so crucial that its importance and relevance are seen through industry and even the United States government. The Department of Homeland Security promotes a solid connection between various industries and the government by supporting awareness campaigns such as National Cybersecurity Awareness Month in addition to encouraging active involvement in measures that can be undertaken by individuals and businesses to protect themselves from threats (Lindsey, 2019). Considering awareness training is a $1 billion per year industry and growing at a rate of 13% (Newcombe, 2016), the results of this research study align with the industry trends and support the growing need for awareness training in all businesses.
Limitations
Survey responses were a result of self-report by the participants and could inherently have bias. This study assumed that participants who completed the survey did so at their own volition and without the assistance of anyone else. Data was analyzed on the assumption that employees understood the questions being asked and answered honestly without thinking about the implications of their answers and how the data captured would reflect on them or their companies.
The HAIS-Q used in the research study can be considered a limitation since the original intent of the questionnaire was to measure information security awareness and not social engineering susceptibility. To the best of the researcher’s knowledge, there is no specific tool that exists to measure social engineering susceptibility. However, the researcher has made the assumption that social engineering susceptibility is comprised of the knowledge, attitude, and behavior of employees as measured in the HAIS-Q. Since the HAIS-Q has been tested for validity and reliability, it is a solid tool to measure the three components that lead someone to fall for social engineering attacks.
Awareness has been suggested to mitigate social engineering attacks (Pyzik, 2015), and it has also been shown to increase employees’ positive attitudes towards information security procedures. Increased awareness leads to a reduction in the occurrence of potentially risky behavior that might impact information security (Parsons, McCormac, Butavicius, et al., 2014). In addition, low information security awareness has been shown to contribute to successful social engineering attacks (Janczewski & Fu, 2010). As a result, a logical inference would be that the higher the score on the HAIS-Q (meaning higher information security awareness), the lower the employee’s susceptibility to social engineering.
This study focused only on small businesses with less than 25 employees in Northeastern Pennsylvania. As a result of the small, limited group that was studied, it may be difficult to generalize the findings in this study to the larger population, different geographic regions, or industries not mentioned here.
Future Research
This research study contributed to the literature on social engineering, especially to the literature on a critical but under-researched population of small businesses. The study also highlights areas for future research on the topic. The HAIS-Q is suggested to continue to be used in other populations to determine if it is an accurate tool to predict social engineering susceptibility. It has been utilized in industries such as government (Parsons, McCormac, Pattinson, et al., 2013), healthcare, retail, education, construction, and manufacturing (Parsons, McCormac, Butavicius, et al., 2014), and in small businesses as part of this research. It would be beneficial to provide this survey to a larger number of employees working in a single industry or repeat the use of the HAIS-Q in a more diverse, geographic region.
This study found areas of significance that require further research and explanation. Awareness training for employees was not found to be a significant predictor of social engineering susceptibility. However, training did show significance, and a positive directional trend was observed in the data suggesting that more training results in a higher knowledge and behavior score. In the supplementary exploration, a negative directional trend was observed in the data suggesting that more training results in a lower susceptibility score. Further research is suggested to confirm or explain these findings.
Other methods can be utilized to validate the results found in this survey such as conducting fabricated social engineering attempts on these small business owners and employees. Studies have been conducted with fabricated phishing emails to study susceptibility to social engineering (Jansson & von Solms, 2013; Goel et al., 2017). Similar studies can be repeated by sending fictitious phishing emails to the small business population studied here and observing and measuring their behavior in response to receiving the emails. Measurements can include whether they clicked on links, opened attachments, or complied with requests in the email. An additional step in the research process to further validate the results of this study would be to attempt to increase the knowledge of employees by offering cybersecurity awareness training in between fabricated phishing attempts to determine if increased knowledge as a result of training really does impact employee behavior.
Other survey mechanisms can be considered to determine whether the HAIS-Q is an appropriate tool to use to measure social engineering susceptibility and whether there is a valid link that can be made between information security awareness and social engineering susceptibility. Other surveys can be given to this same small business population and results can be compared to the results found here to confirm that demographic characteristics do not predict social engineering susceptibility.
Even though the results suggest that demographic characteristics are not significant predictors of social engineering susceptibility, it is well-known that employees are susceptible to some extent based on the success of social engineering attacks. Future research may focus on trying to find what the other predictors of social engineering susceptibility are since demographic characteristics, according to this study, only account for 6.8% of an individual’s susceptibility to these types of attacks.
The recent global pandemic has seen an unprecedented amount of work, socialization, and interaction occur electronically. The Federal Bureau of Investigation (FBI) has issued warnings regarding the increase in social engineering schemes, from those attempting to gain money or acquire personal health information (FBI, 2020; Proofpoint, 2021). Venkatesha, Reddy, & Chandavarkar (2021) have noted that the need for human connection, which has been lacking due to social distancing and the closure of offices and schools, coupled with the increased use of the Internet provided the perfect opportunity for social engineers to capitalize on the new way of daily life. Repeating this research study in a post-pandemic world would provide valuable insight as to whether information security awareness has increased, decreased, or stayed the same when considering the disruptions to individuals’ work and home life.
Conclusion
Social engineering attacks have become more common in today’s interconnected world on both an individual and a business level. When businesses are victims of social engineering attacks, the impact can be far-reaching and affect not only the business, but its customers, vendors, shareholders, and society as a whole. Small businesses comprise the majority of businesses in the United States and are not immune to the effects of social engineering. Demographic characteristics were studied to determine if they are significant predictors of social engineering susceptibility in owners and employees of small businesses in Northeastern Pennsylvania. Even though demographics were not shown to be significant predictors, these findings have several implications for small businesses and how they can protect themselves from the growing threat of social engineering attacks.
References
- Aguilar, L. (2015). The need for greater focus on the cybersecurity challenges facing small and midsize businesses. U.S. Securities and Exchange Commission. Retrieved from https://www.sec.gov/news/statement/cybersecurity-challenges-for-smallmidsize-businesses.html#_edn6
- Airehrour, D., Nair, N., & Madanian, S. (2018). Social engineering attacks and countermeasures in the New Zealand banking system: Advancing a user-reflective mitigation model. Information, 9(5), 10. doi: 10.3390/info9050110
- Algarni, A., Xu, T., & Chan, T. (2015). Susceptibility to social engineering in social networking sites: The case of Facebook. 36th International Conference on Information Systems (ICIS2015), 13-16. Retrieved from https://pdfs.semantic.org/055c/cd809b80a3d2e8e813acd 81ddb98de8c3c7a.pdf?_ga=2.165038463.1746211815.1548784731-797035428.1548784731
- Ashford, W. (2016). Social engineering is top hacking method, survey shows. ComputerWeekly.com. Retrieved from https://www.computerweekly.com/news/4500272941/Social-engineering-is-top-hacking-method-survey-shows
- Bullee, J., Montoya, L., Pieters, W., Junger, M., & Hartel, P. (2015). The persuasion and security awareness experiment: Reducing the success of social engineering attacks. Journal of Experimental Criminology, 11, 97-115. doi: 10.1007/s11292-0149222-7
- Butavicius, M., Parsons, K., Pattinson, M., & McCormac, A. (2015). Breaching the human firewall: Social engineering in phishing and spear-phishing emails. Australasian Conference on Information Systems. Retrieved from https://www.researchgate. net/publications/303812216_Breaching_the_Human_Firewall_ Social_enginneering_in_Phishing_and_Spear-Phishing_Emails
- Cheung-Blunden, V., Cropper, K., Panis, A., & Davis, K. (2018). Functional divergence of two threat-induced emotions: Fear-based versus anxiety-based cybersecurity preferences. Emotion. https://doi.org/10.1037/emo0000508
- Cialdini, R. (2007). Influence: The Psychology of Persuasion. New York, NY. Harper Collins.
- Data Breach Investigations Report (DBIR). (2021). Verizon. Retrieved from https://enterprise.verizon.com/resources/reports/2021-data-breach-investigations-report.pdf
- Federal agencies warn of emerging fraud schemes related to COVID-19 vaccines. (2020). Retrieved from https://www.fbi.gov/news/pressrel/press-releases/federal agencies-warn-of-emerging-fraud-schemes
- Flores, W., Holm, H., Svensson, G., Ericsson, G. (2013). Using phishing experiments and scenario-based surveys to understand security behavior. Information Management and Computer Security, 22(4), 393-406. doi: 10.1108/IMCS-11-20130083
- FSB. (2016). Cyber resilience: How to protection small firms in the digital economy. Retrieved from https://www.fsb.org.uk/docs/default-source/fsb-org-uk/FSB-CyberResilience-report2016.pdf?sfvrsn=0
- Goel, S., Williams, K., & Dincelli, E. (2017). Got phished? Internet security and human vulnerability. Journal of the Association for Information Systems, 18(1), 22-44. Retrieved from Academic Search Premier.
- Grassegger, T. & Nedbal, D. (2021). The role of employees’ information security awareness on the intention to resist social engineering. Procedia Computer Science, 181, 59-66. https://doi.org/10.1016/j.procs.2021.01.103
- Guadagno, R., Muscanell, N., Rice, L., & Roberts, N. (2013). Social influence online: The impact of social validation and likability on compliance. Psychology of Popular Media Culture, 2(1), 51 -60. doi: 10.1037/a0030592
- Halevi, T., Memon, N., & Nov, O. (2015). Spear-phishing in the wild: A real-world study of personality, phishing self-efficacy, and vulnerability to spear-phishing. SSRN Electronic Journal, doi: 10.2139/ssrn.2544742
- Happ, C., Melzer, A., & Steffgen, G. (2016). Trick with treat – Reciprocity increases the willingness to communicate personal data. Computers in Human Behavior, 61, 372 – 377. http://dx.doi.org/10.1016/j.chb.2016.03.026
- Harris, S. (2018). Cyber security threats against small businesses on the rise in 2018. Idaho State Journal
- Heartfield, R. & Loukas, G. (2015). A taxonomy of attacks and a survey of defense mechanisms for semantic social engineering attacks. ACM Computing Surveys, 48(3), doi:10.1145/2835375
- Hiscox (2018). Small business cyber risk report. Retrieved from https://www.hiscox.com/documents/2018-Hiscox-Small-Business-Cyber-Risk-Report.pdf
- Jackson, R. (2018). Pulling strings. Internal Auditor, 75(4), 34 – 39. Retrieved from Business Source Premier.
- Jagatic, T., Johnson, N., Jakobsson, M., & Menczer, F. (2007). Social phishing. Communications of the ACM, 50(10), 94 – 100. doi: 10.1145/1290958.1290968.
- Janczewski, L. & Fu, L. (2010). Social engineering-based attacks: Model and New Zealand perspective. Proceedings of the International Multiconference on Computer Science and Information Technology. Retrieved from https://annals-csis.org/proceeddings /2010/pliks/36.pdf
- Jansson, K. & von Solms, R. (2013). Phishing for phishing awareness. Behavior & Information Technology, 32(6), 584-593. doi: 10.1080/0144929X.2011.632650
- LeClair, J. (2015). Testimony before U.S. House of Representatives. Retrieved from https://docs.house.gov/meetings/SM/SM00/20150422/103276/HHRG-114-SM0020150422-SD003-U4.pdf
- Let’s talk about social engineering small businesses. (2018). Social-Engineer. Retrieved from https://www.social-engineer.com/lets-talk-about-social-engineering-smallbusinesses/
- Lindsey, N. (2019). Organizations are embracing cyber security awareness training as the first line of defense against hackers. CPO Magazine. Retrieved from https://www.cpomagazine.com/cyber-security/organizations-are-embracing-cyber-securityawareness-training-as-the-first-line-of-defense-against-hackers
- Mitnick, K. & Simon, W. (2003). The art of deception. Indianapolis, IN. Wiley.
- Moody, G., Galletta, D., & Dunn, B. (2017). Which phish get caught? An exploratory study of individuals’ susceptibility to phishing. European Journal of Information Systems, 26, (6), 564 – 584. https://doi.org/10.1057/s41303-017-0058-x
- Montanez, R., Golob, E., Xu, S. (2020). Human cognition through the lens of social engineering cyberattacks. Frontiers in Psychology, 11, 1755. doi: 10.3389/fpsyg2020.01755
- Newcombe, T. (2016). Can security awareness training change behavior and reduce risk? Government Technology. Retrieved from https://www.govtech.com/security/Can-Security-Awareness-Training-Change-Behavior-and-ReduceRisk.html
- Parsons, K., Calic, D., Pattinson, M., Butavicius, M., McCormac, A., & Zwaans, T. (2017). The human aspects of information security questionnaire (HAIS-Q): Two further validation studies. Computers & Security, 66, 40-51. https://dx.doi.org/10.1016/j.cose.2017.01.004
- Parsons, K., McCormac, A., Pattinson, M., Butavicius, M., & Jerram, C. (2013). An analysis of information security vulnerabilities at three Australian government organizations. Proceedings of the European Information Security Multi-Conference (EISMC 2013). Retrieved from https://pdfs.semanticscholar.org/fc19/b83fc2831669d07e37131e1e8a4616b945a0.pdf
- Parsons, K., McCormac, A., Butavicius, M., Pattinson, M., & Jerram, C. (2014). Determining employee awareness using the human aspects of information security questionnaire (HAIS-Q). Computers & Security, 42, 165-176. doi:10.1016/j.cose.2013.12.003
- Pattinson, M., Butavicius, M., Parsons, K., McCormac, A., & Calic, D. (2017). Managing information security awareness at an Australian bank: A comparative study. Information & Computer Security, 25(2), 181-189. doi: 10.1108/ICS-03-20170017.
- Proofpoint Threat Research Team (2021). Attackers use COVID-19 vaccine lures to spread malware, phishing, and BEC. Retrieved fromhttps://www.proofpoint.com/us/blog/threat-insight/attackers-usecovid-19-vaccine-lures-spread-malware-phishing and-bec
- Pyzik, K. (2015). Shutting the door on social engineering. Internal Auditor, 72(5), 20 – 21. Retrieved from Business Source Premier.
- Salerno, J. & Peter-Hagene, L. (2015). One angry woman: Anger expression increases Influence for men, but decreases influence for women, during group deliberation. Law and Human Behavior, 39(6), 581 – 592. doi: 10.1037/lhb0000147
- Sheng, S., Holbrook, M., Kumaraguru, P., Cranor, L., & Downs, J. (2010). Who falls for phish? A demographic analysis of phishing susceptibility and effectiveness of interventions. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems.
- SBA – Small Business Profile (2018). U.S. Small Business Administration Office of Advocacy. Retrieved from https://www.sba.gov/sites/default/files/advocacy/2018Small-Business Profiles-US.pdf
- Sumner, A., Yuan, X., Anwar, M. & McBride, M. (2022). Examining factors impacting the effectiveness of anti-phishing trainings. Journal of Computer Information Systems, 62(5), 975-997. Doi: 10.1080/08874417.2021.1955638
- Snyman, D. & Kruger, H. (2016). Behavioural thresholds in the context of information security. Proceedings of the Tenth International Symposium on Human Aspects of Information Security & Assurance. Retrieved from https://www.researchgate.net/publications/314838010_Behavioural_Thresholds_in_the_ Context_of_Information_Security
- Tetri, P. & Vuorinen. (2013). Dissecting social engineering. Behavior & Information Technology, 32(10). doi: 10.1080/0144929X.2013.763860
- Uebelacker, S. & Quiel, S. (2014). The social engineering personality framework, presented at the Workshop on Socio-Technical Aspects in Security and Trust, Vienna, 2014. doi:10.1109/stast.2014.12
- Van Kleef, G., van den Berg, H., & Heerdink, M. (2015). The persuasive power of emotions: Effects of emotional expressions on attitude formation and change. American Psychological Association, 100(4), 1124 – 1142. http://dx.doi.org/10.1037/apl0000003
- Venkatesha, S., Reddy, K., & Chandavarkar, B. (2020). Social engineering attacks during the COVID-19 pandemic. SN Computer Science, 2(2), 78. doi: 10.1007/s42979-020-00443-1
- Vishwanath, A., Harrison, B., & Ng, Y. (2016). Suspicion, cognition, and automaticity model of phishing susceptibility. Communication Research, 45(8), 1-21. doi: 10.117/0093650215627483
- Vishwanath, A., Herath, T., Chen, R., Wang, J., & Rao, H. (2011). Why do people get phished? Testing individual differences in phishing vulnerability within an integrated information processing model. Decision Support Systems. 51(3), 576-586. doi: 10/1016/j.dss.2011.103002
- Williams, E., Hinds, J., & Joinson, A. (2018). Exploring susceptibility to phishing in the workplace. International Journal of Human-Computer Studies, 120, 1-13. https://doi.org/10.1016/j.ijhcs.2018.06.004
- Wright, R., Chakraborty, S., Basoglu, K., & Marett, K. (2010). Where did they go right? Understanding the deception in phishing communications. Group Decision and Negotiation, 19(4), 391 – 416. doi: 10.1007/s10726-009-9167-9.
- Zheng, Y., Robertson, T., Yan, R., Park, S., Bordoff, S., Chen, Q., & Sprissler, E. (2018). Finding the weakest links in the weakest link: How well do undergraduate students make cybersecurity judgment? Computers in Human Behavior, 84, 375-382. https://doi.org/10.1016/j.chb2018.02 019
Tables & Figures
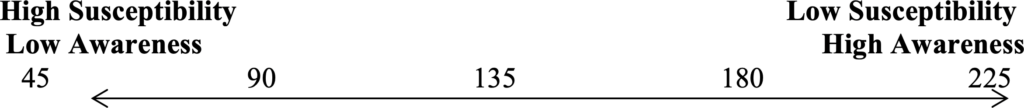
Figure 1. Modified HAIS-Q scoring. This figure provides the range of possible scores on the modified version of the HAIS-Q, ranking respondents from low to high susceptibility to social engineering.
Table 1. Multivariate regression
results of all independent variables
| Coefficient | Std. Error | Beta | t | p | |
| a (y-intercept) | 37.63 | 11.34 | – | 3.32 | < .05 |
| b (Age) | -0.10 | 0.13 | -.10 | -0.73 | .46 |
| c (Gender) | -1.18 | 3.14 | -.05 | -0.38 | .71 |
| d (Associate / Bachelor) | -5.86 | 4.41 | -.24 | -1.33 | .19 |
| e (Master / Terminal) | -6.07 | 4.66 | -.24 | -1.30 | .20 |
| f (Employment Length) | 3.67 | 3.25 | .15 | 1.13 | .26 |
| g (Training) | -1.83 | 2.82 | -.08 | -0.65 | .52 |
| h (Weekly Hours) | -0.10 | 0.10 | -.11 | -0.94 | .35 |
| i (Cultural Identity) | -0.85 | 5.42 | -.02 | -0.16 | .88 |
| j (Industry) | 0.47 | 3.34 | .02 | 0.14 | .89 |
| k (Rank) | -1.46 | 3.04 | -.06 | -.48 | .63 |
Table 2. Multivariate Regression
Results: Knowledge as a predictor of attitude
| Coefficient | Std. Error | Beta | t | p | |
| a (y-intercept) | 33.28 | 3.42 | – | 9.74 | < .001 |
| b (Knowledge Score) | .541 | .06 | .70 | 9.39 | < .001 |
Table 3. Multivariate Regression Results:
Attitude as a predictor of behavior
| Coefficient | Std. Error | Beta | t | p | |
| a (y-intercept) | 13.53 | 5.00 | – | 2.70 | < .05 |
| b (Attitude Score) | .75 | .08 | .71 | 9.81 | < .05 |
Table 4. Multivariate Regression Results – Knowledge and attitude as a predictor of behavior
| Coefficient | Std. Error | Beta | t | p | |
| a (y-intercept) | 13.48 | 4.32 | – | 3.12 | < .05 |
| b (Knowledge Score) | .41 | .07 | .50 | 5.73 | < .05 |
| c (Attitude Score) | .38 | .09 | .36 | 4.14 | < .05 |
Table 5. Susceptibility Score – Mean and standard deviations for training on average per year
| n | Mean Susceptibility Score | Standard Deviation | |
| No Training | 39 | 24.02 | 11.01 |
| One Time | 30 | 24.18 | 12.30 |
| Two Times | 6 | 18.89 | 12.50 |
| Three Times | 7 | 15.00 | 9.63 |
| More than 3 Times | 13 | 13.97 | 13.15 |
Table 6: Susceptibility Score – Mean and Standard Deviations for Training (Recode) on Average Per Year
| n | Mean Susceptibility Score | Standard Deviation | |
| No Training | 39 | 24.02 | 11.01 |
| 1 -3 Times | 43 | 21.95 | 12.21 |
| More than 3 Times | 13 | 13.97 | 13.16 |
Figure 2. HAIS-Q Responses
HAIS-Q Responses
| Knowledge | Strongly Disagree | Disagree | Neither Agree nor Disagree | Agree | Strongly Agree |
| It is acceptable to use my social media passwords on my work accounts. | 47 (49%) | 25 (26%) | 9 (9%) | 13 (14%) | 1 (1%) |
| I am allowed to share my work passwords with colleagues. | 41 (43%) | 25 (26%) | 14 (15%) | 11 (12%) | 4 (4%) |
| A mixture of letters, numbers, and symbols is necessary for work passwords. | 6 (6%) | 5 (5%) | 1 (1%) | 40 (42%) | 43 (45%) |
| I am allowed to click on any links in emails from people I know. | 24 (25%) | 17 (18%) | 17 (18%) | 34 (36%) | 3 (3%) |
| I am not permitted to click on a link in an email from an unknown sender. | 8 (8%) | 10 (10%) | 12 (13%) | 28 (29%) | 37 (39%) |
| I am allowed to open email attachments from unknown senders. | 45 (47%) | 19 (20%) | 10 (10%) | 14 (15%) | 7 (7%) |
| I am allowed to download any files onto my work computer if they help me to do my job. | 29 (30%) | 18 (19%) | 9 (9%) | 28 (29%) | 11 (12%) |
| While I am at work, I shouldn’t access certain websites. | 4 (4%) | 2 (2%) | 5 (5%) | 32 (34%) | 52 (55%) |
| I am allowed to enter any information on any website if it helps me do my job. | 28 (29%) | 27 (28%) | 15 (16%) | 18 (19%) | 7 (7%) |
| When working in a public place, I have to keep my laptop with me at all times. | 6 (6%) | 8 (8%) | 12 (13%) | 29 (30%) | 40 (42%) |
| I am allowed to send sensitive work files via a public Wi-Fi network. | 42 (44%) | 20 (21%) | 20 (21%) | 11 (12%) | 2 (2%) |
| When working on a sensitive document, I must ensure that strangers can’t see my laptop screen. | 1 (1%) | 13 (14%) | 7 (7%) | 37 (39%) | 37 (39%) |
| Sensitive print-outs can be disposed of in the same way as non-sensitive ones. | 55 (58%) | 25 (26%) | 3 (3%) | 7 (7%) | 5 (5%) |
| If I find a USB stick in a public place, I shouldn’t plug it into my work computer. | 7 (7%) | 0 (0%) | 6 (6%) | 19 (20%) | 63 (66%) |
| I am allowed to leave print-outs containing sensitive information on my desk overnight. | 42 (44%) | 27 (28%) | 8 (8%) | 10 (10%) | 8 (8%) |
| Attitude | Strongly Disagree | Disagree | Neither Agree nor Disagree | Agree | Strongly Agree |
| It is safe to use the same passwords for social media and work accounts. | 48 (50%) | 30 (32%) | 9 (9%) | 8 (8%) | 0 (0%) |
| It’s a bad idea to share my work passwords, even if a colleague asks for it. | 2 (2%) | 7 (7%) | 10 (10%) | 42 (44%) | 34 (36%) |
| It’s safe to have a work password with just letters. | 44 (46%) | 43 (45%) | 5 (5%) | 3 (3%) | 0 (0%) |
| It’s always safe to click on links in emails from people I know. | 34 (36%) | 40 (42%) | 11 (12%) | 9 (9%) | 1 (1%) |
| Nothing bad can happen if I click on a link in an email from an unknown sender. | 78 (82%) | 16 (17%) | 0 (0%) | 1 (1%) | 0 (0%) |
| It’s risky to open an email attachment from an unknown sender. | 1 (1%) | 1 (1%) | 2 (2%) | 29 (30%) | 62 (65%) |
| It can be risky to download files on my work computer. | 1 (1%) | 3 (3%) | 7 (7%) | 40 (42%) | 44 (46%) |
| Just because I can access a website at work, doesn’t mean that it’s safe. | 1 (1%) | 0 (0%) | 0 (0%) | 45 (47%) | 49 (52%) |
| If it helps me to do my job, it doesn’t matter what information I put on a website. | 40 (42%) | 40 (42%) | 5 (5%) | 10 (10%) | 0 (0%) |
| When working in a café, it’s safe to leave my laptop unattended for a minute. | 59 (62%) | 30 (32%) | 4 (4%) | 1 (1%) | 1 (1%) |
| It’s risky to send sensitive work files using a public Wi-Fi network. | 5 (5%) | 1 (1%) | 3 (3%) | 42 (44%) | 44 (46%) |
| Disposing of sensitive print-outs by putting them in trash bins is safe. | 3 (3%) | 2 (2%) | 7 (7%) | 42 (44%) | 41 (43%) |
| If I find a USB stick in a public place, nothing bad can happen if I plug it into my work computer. | 58 (61%) | 26 (27%) | 6 (6%) | 2 (2%) | 3 (3%) |
| It’s risky to leave print-outs that contain sensitive information on my desk overnight. | 74 (78%) | 15 (16%) | 2 (2%) | 2 (2%) | 2 (2%) |
| Behavior | Strongly Disagree | Disagree | Neither Agree nor Disagree | Agree | Strongly Agree |
| I use different passwords for social media and work accounts. | 2 (2%) | 9 (9%) | 6 (6%) | 32 (34%) | 46 (48%) |
| I share my work passwords with colleagues. | 37 (39%) | 30 (32%) | 10 (10%) | 16 (17%) | 2 (2%) |
| I use a combination of letters, numbers, and symbols in my work passwords. | 3 (3%) | 2 (2%) | 1 (1%) | 35 (37%) | 54 (57%) |
| I don’t always click on links in emails just because they come from someone I know. | 3 (3%) | 6 (6%) | 4 (4%) | 49 (52%) | 33 (35%) |
| If an email from an unknown sender looks interesting, I click on a link within it. | 62 (65%) | 23 (24%) | 7 (7%) | 1 (1%) | 2 (2%) |
| I don’t open email attachments if a sender is unknown to me. | 7 (7%) | 2 (2%) | 11 (12%) | 22 (23%) | 53 (56%) |
| I download any files onto my work computer that will help me get the job done. | 23 (24%) | 33 (35%) | 14 (15%) | 20 (21%) | 5 (5%) |
| When accessing the internet at work, I visit any website that I want to. | 29 (30%) | 34 (36%) | 13 (14%) | 15 (16%) | 4 (4%) |
| I assess the safety of websites before entering information. | 3 (3%) | 8 (8%) | 8 (8%) | 41 (43%) | 35 (37%) |
| When working in a public space, I leave my laptop unattended. | 62 (65%) | 26 (27%) | 6 (6%) | 1 (1%) | 0 (0%) |
| I send sensitive work files using a public Wi-Fi network. | 48 (50%) | 27 (28%) | 14 (15%) | 6 (6%) | 0 (0%) |
| I check that strangers can’t see my laptop screen if I’m working on a sensitive document. | 3 (3%) | 3 (3%) | 15 (16%) | 40 (42%) | 34 (36%) |
| When sensitive print-outs need to be disposed of, I ensure that they are shredded or destroyed. | 5 (5%) | 0 (0%) | 6 (6%) | 29 (30%) | 55 (58%) |
| I wouldn’t plug a USB stick found in a public place into my work computer. | 2 (2%) | 1 (1%) | 3 (3%) | 18 (19%) | 71 (75%) |
| I leave print-outs that contain sensitive information on my desk when I’m not there. | 41 (43%) | 31 (33%) | 8 (8%) | 10 (10%) | 5 (5%) |
Figure 3. Demographic Questions
1) Do you work for a small business in Northeastern Pennsylvania that employs less than 25 people?
- Yes
- No
2) Do you have a company email address?
- Yes
- No
3) What is your gender?
- Male
- Female
- Other
- Prefer Not to Answer
4) What is your age?
5) What is the highest level of education you have received?
- Less Than High School
- High School Diploma
- Associate Degree
- Bachelor’s Degree
- Master’s Degree
- Terminal Degree
6) How long have you worked for your current company?
- Less than 1 year
- 1 – 3 years
- 4 – 6 years
- 7 – 9 years
- 10 or more years
7) What is the average number of hours per week that you work?
8) In what industry do you work?
- Healthcare
- Marketing
- Construction
- Technology
- Nonprofit
- Law
- Finance
- Insurance
- Other
9) Thinking about the last three years, how many times per year on average have you received training or education on cyber security awareness?
- 0
- 1 time
- 2 times
- 3 times
- More than 3 times
10) What is your rank in the company?
- Owner / Highest Ranking Official
- Non-Owner / Non-Highest Ranking Official
11) Which of the following represents the cultural identity with which you most identify?
- American
- Latino
- Asian
- Indian
- Canadian
- British / European
- Middle Eastern
- African
- Other
